What Is a Hardware Security Module (HSM) and Why Does It Matter?
Every digital interaction you rely on such as logging into a bank account, signing a software update, or submitting a government form depends on trust.
You trust that:
- The system you’re communicating with is legitimate
- Your data remains private
- The information hasn’t been altered
That trust isn’t abstract; it’s built on cryptography.
At the heart of cryptography are cryptographic keys the digital secrets that encrypt data, prove identities, and authorize transactions. If those keys are stolen, copied, or manipulated, trust collapses instantly: Systems can be impersonated, data decrypted, and transactions forged, often without any warning.
This is why Hardware Security Modules (HSMs) exist: to protect cryptographic keys at the highest possible level.
What Is a Hardware Security Module (HSM)?
A Hardware Security Module (HSM) is a purpose-built physical security device designed to:
- Generate cryptographic keys securely
- Protect those keys throughout their entire lifecycle
- Perform sensitive cryptographic operations inside secure hardware
Unlike software-based security tools that run on general-purpose servers, a Hardware Security Module (HSM) is dedicated hardware engineered for one job: protecting the most sensitive secrets in a digital system.
Because HSMs are hardware, they can enforce protections that software alone cannot, including resistance to tampering, physical attacks, and insider threats.
HSMs act as the root of trust that everything else depends on in modern digital infrastructure.
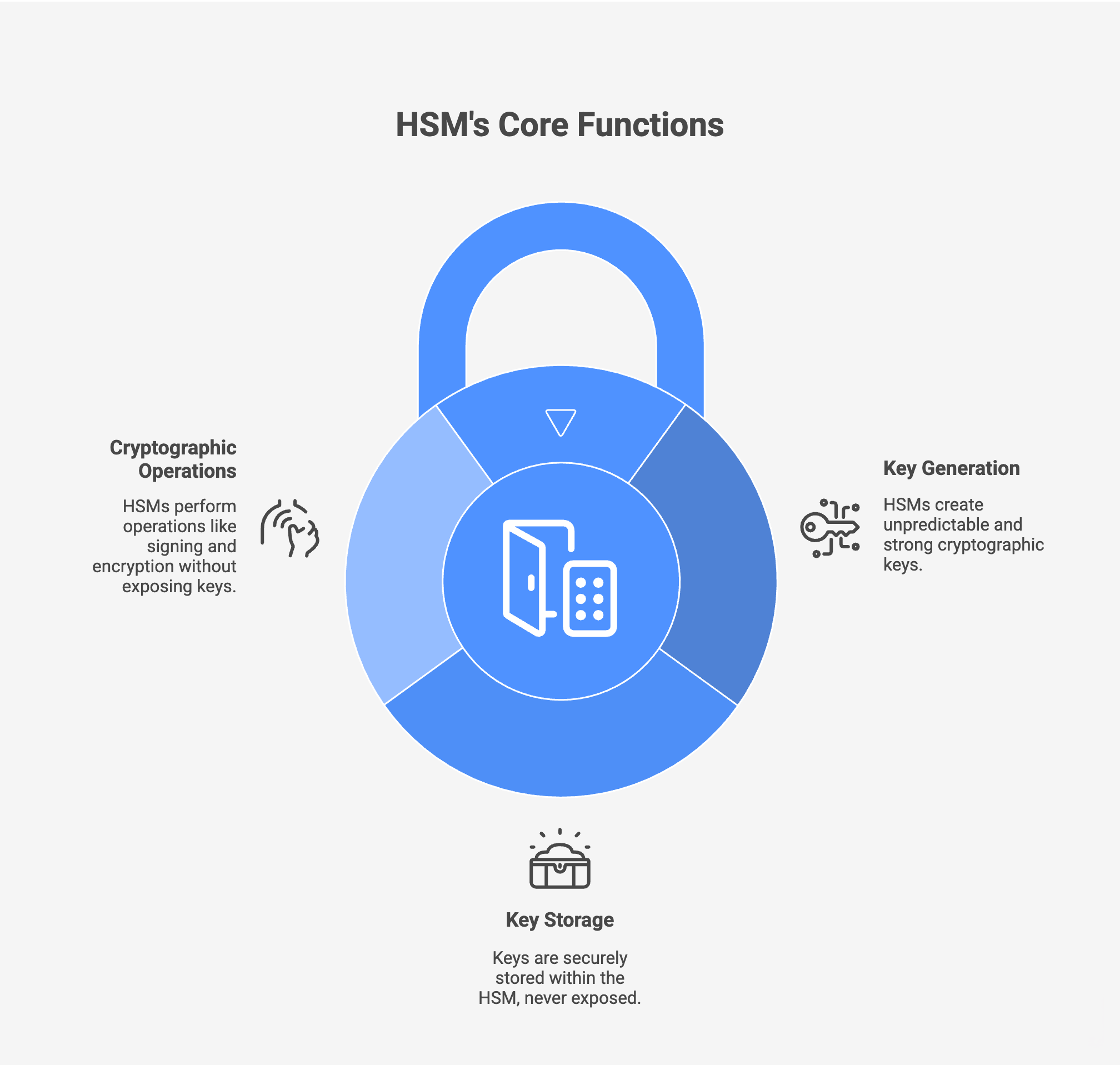
What Does an HSM Do?
While the internals of an HSM are highly technical, its role can be broken down into three core functions.
1. Securely Generate Cryptographic Keys
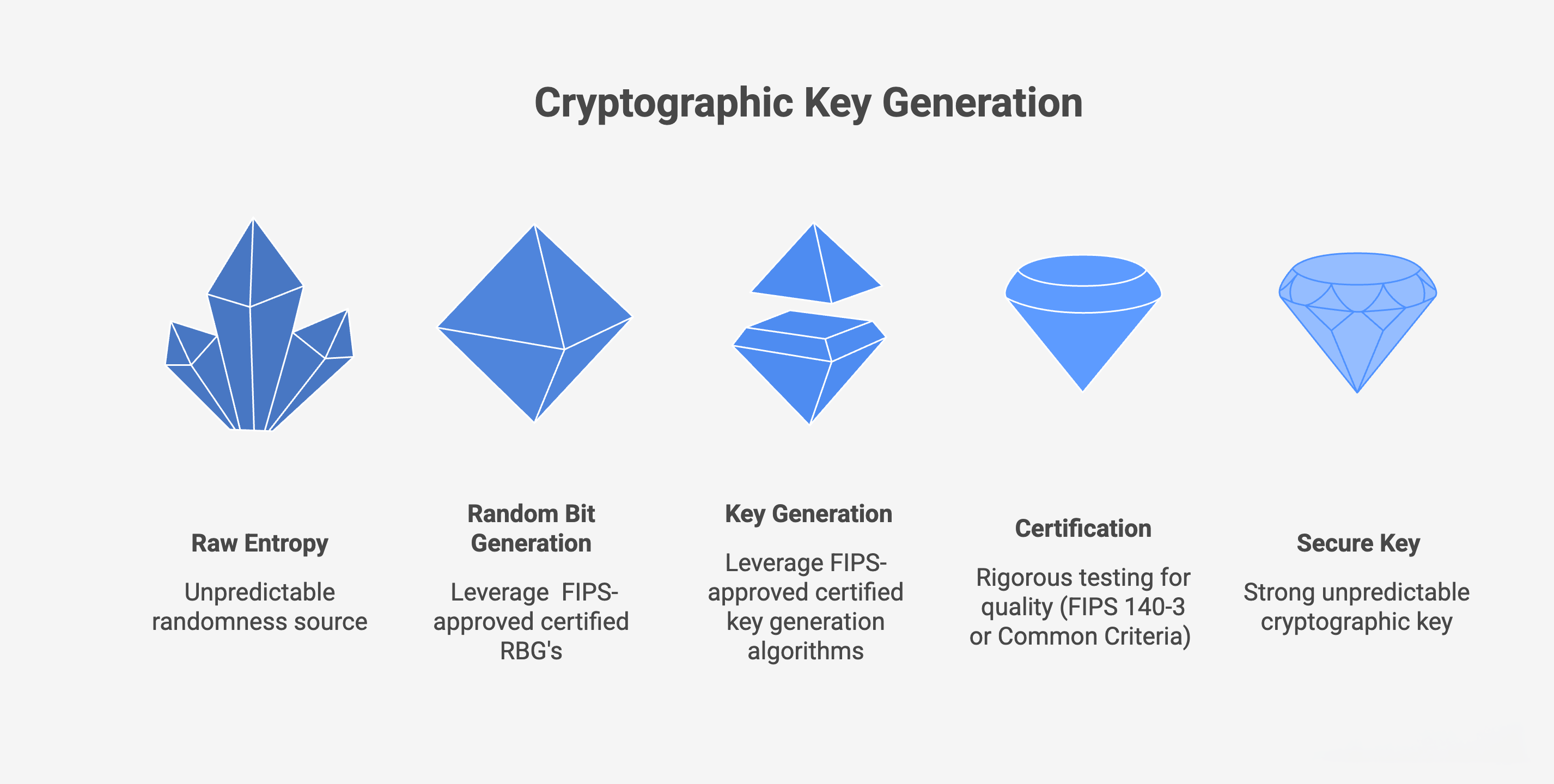
HSMs generate cryptographic keys inside the device using high-quality sources of randomness (also known as entropy). This ensures keys are unpredictable and cryptographically strong from the moment they are created.
During certification processes such as NIST FIPS 140-3 or Common Criteria, an HSM’s entropy sources and key generation processes are rigorously tested to ensure they meet strict quality standards.
While quantum random number generators (QRNGs) can be used, they are not required. High-quality non-QRNG entropy sources have been successfully used in HSMs for decades.
2. Protect and Store Keys Securely
Once generated, cryptographic keys never leave the HSM in plaintext form.
Keys are stored in protected memory inside the device and are never exposed to:
- The operating system
- Applications
- Cloud administrators or system operators
HSMs use a combination of physical and logical security controls, including tamper detection. If an attack is detected, the device can automatically zeroize (delete) its keys, ensuring it fails safely rather than allowing secrets to be compromised.
3. Perform Cryptographic Operations Safely
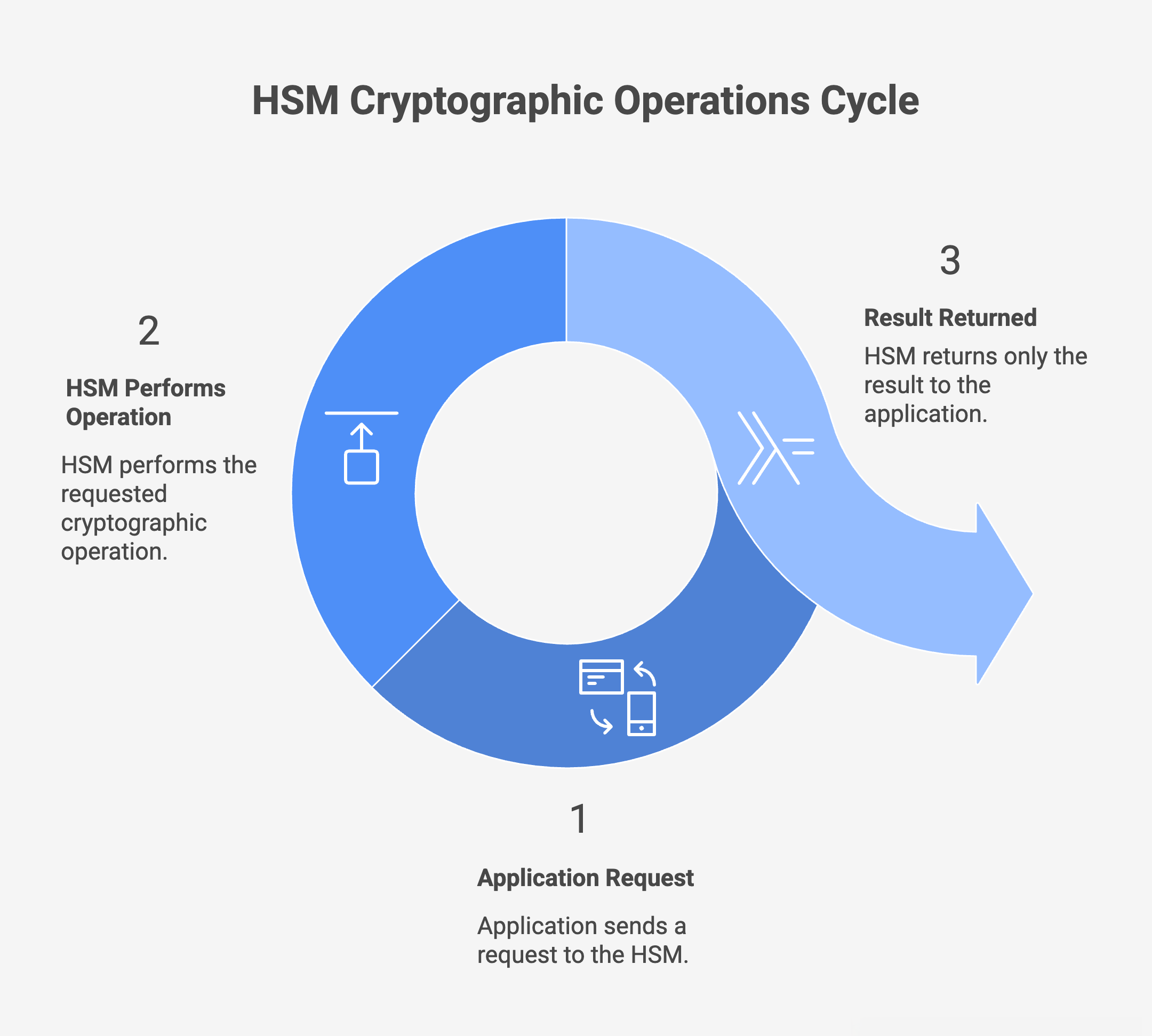
Instead of handing keys to applications, an HSM performs cryptographic operations on their behalf, including:
- Digitally signing data and transactions
- Encrypting and decrypting sensitive information
- Verifying identities and authenticating systems
Applications send requests such as “sign this transaction” or “decrypt this message.” The HSM performs the operation internally and returns only the result—never the key itself.
The correctness and integrity of these operations are validated through independent programs such as NIST’s Cryptographic Algorithm Validation Program (CAVP).
Why Hardware Matters for Security
The defining difference between an HSM and software-only key management is hardware-enforced protection.
Because an HSM is a dedicated physical device, it can:
- Detect probing or tampering attempts
- Shut down or erase keys if an attack is detected
- Enforce security boundaries that software cannot bypass
Even administrators with full server access cannot extract usable keys from a properly configured HSM. This dramatically reduces the attack surface compared to software-based key storage, where malware or insider threats may allow attackers to gain access.
In short: hardware enforces trust where software alone cannot.
Where Are HSMs Used Today?
Hardware Security Modules are deeply embedded in today’s digital infrastructure, even if most people never see them.
Common use cases include:
-
Banking and financial systems
Protecting payment keys and transaction signing that enable the digital economy -
Government systems
Securing identities, records, and classified data -
Cloud and data centers
Protecting encryption keys for stored and transmitted data -
Public Key Infrastructure (PKI)
Protecting certificate authority keys that enable identity and trust on the Internet -
Critical infrastructure
Securing telecommunications, energy systems, and other essential services
Any environment that depends on strong identity, confidentiality, or integrity at scale relies on HSMs behind the scenes.
Why HSMs Are Foundational to Digital Trust
Strong cryptographic algorithms alone are not enough. Trust also depends on how well the keys behind those algorithms are protected.
HSMs provide a trusted foundation for:
- Regulatory and compliance requirements
- Long-term key protection
- Auditable, controlled cryptographic operations
By isolating keys in tamper-resistant hardware, organizations can demonstrate that security is enforced by design, not just by policy.
This is why HSMs are a cornerstone of secure architectures, both today and into the future.
Looking Ahead: HSMs in a Post-Quantum World
Hardware Security Modules and Post-Quantum Cryptography
Quantum computing, while still emerging, has the potential to break many of today’s cryptographic algorithms, particularly those used for digital signing and key agreement.
This will require updates across most cryptographic infrastructure, including HSMs. Preparing for that future does not mean replacing everything overnight, it means building on platforms that can adapt. That adaptability is known as cryptographic agility.
The next generation of HSMs is being designed with longevity and adaptability in mind. These systems can support new cryptographic algorithms as standards evolve, allowing organizations to transition to quantum-resistant methods without replacing their entire security infrastructure.
Unfortunately, many previous-generation HSMs were not built with the necessary foundational trust elements, fittingly known as Roots of Trust (RoTs), required to securely support future updates and upgrades.
In that sense, next-generation HSMs are not just secure for today; they are a foundation for what comes next.
Conclusion: The Simple Takeaway
Cryptography enables digital trust, and cryptographic keys make cryptography work. If keys are compromised, trust fails.
Hardware Security Modules exist to prevent that failure. By generating, storing, and using cryptographic keys inside secure hardware, HSMs protect the digital systems we depend on every day.
Cryptographic agility ensures HSMs can securely adapt over time to meet both today’s and tomorrow’s security needs.
In plain terms: if trust matters, hardware matters, and HSMs are where that trust begins.
Explore Crypto4A's Next-Generation HSM Solutions
Crypto4A builds quantum-safe, crypto-agile Hardware Security Modules designed to protect your organization today and into the post-quantum future.
-
QxHSM™ — A FIPS-validated, quantum-first HSM built for crypto-agility, interoperability, and cryptographic portability.
-
QxVault™ — An integrated secrets management vault with a built-in HSM, protecting credentials, secrets, and API keys with hardware-enforced security.
Discover which solution is right for you →
Crypto4A is a Canadian cybersecurity company pioneering quantum-safe hardware security modules (HSMs) and infrastructure solutions designed to safeguard the digital world today and tomorrow. Trusted by enterprises, governments, and infrastructure providers across the globe, we specialize in crypto-agility, scalability, portability, and post-quantum cryptography.